This is one of the best epic fail stories regarding security and involves different levels regarding the protection itself.
First of all, let’s see what the company says about that:

We will come back to this later…
Now, let’s see what happens every time we try to open a protected executable:
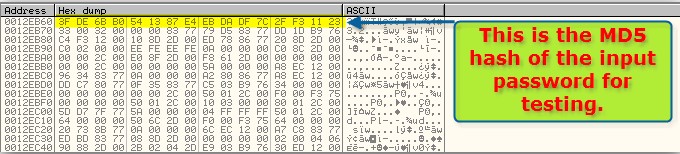
The protection calculates the MD5 hash of the password we put for testing….
…and it has also loaded in memory the MD5 hash of the correct password.

As a first solution, a quick attack would be just to copy the MD5 hash of the correct password in the memory location where the MD5 hash of the dummy password is loaded and you are done.
But, wait a minute…
How does the protection know at this point the MD5 hash of the real password?
Let’s use a hex editor:

Oh, yes the protection has stored the MD5 hash of the password used to lock the executable inside the protected executable.
As a second solution, you can modify the protected executable itself and replace that hash with the one of a known password.
Did anyone buy that?!?! :O)
[social_share/]
